By
Rivka Hoffnung – Cloud Security Architect, CYMOTIVE Technologies ![]()
Stav Hefetz – Cloud Security Architect, CYMOTIVE Technologies ![]()
Introduction
As technology evolves, so too does the automotive industry. Autonomous vehicles, driven by state-of-the-art Artificial Intelligence (AI), are swiftly transitioning from novelty to norm. AI models and deep learning algorithms are revolutionizing how vehicles interact with their environment, thus facilitating safer and more efficient driver navigation that avoids accidents and saves lives.
In this article, we’ll explore the AI models and deep learning techniques that empower both current and upcoming vehicles, spearheading the autonomous vehicle revolution. We’ll also discuss the inherent risks associated with this powerful technology, as demonstrated in our Proof of Concept (PoC).
AI Technology’s Role in the Automotive Industry
Artificial Intelligence (AI) technology in the automotive industry refers to the integration of machine learning algorithms and advanced computer systems into vehicles, allowing vehicles to operate autonomously. It involves leveraging sensors, cameras, and radar to collect data from the vehicle’s environment. This enables the recognition of elements such as road signs, pedestrians and other vehicles while real-time processing of this data to make informed critical decisions that ensure safety and directly impact human lives.
AI technology in autonomous vehicles is powered by machine learning models that are trained to recognize patterns, detect objects, and interpret complex data. These models are continuously learning and improving according to acquired data in order to adjust to shifting road conditions, foresee potential hazards and make split-second decisions.
One of the key elements of AI technology in the automotive industry is deep learning. Deep learning algorithms employ multilayered neural networks to process, analyze and interpret vast amounts of data, equipping vehicles with the ability to accurately perceive their surroundings and respond accordingly.
The implementation of AI technology in the automotive industry has revolutionized the way vehicles interact with their surroundings. This evolution has the potential to significantly enhance road safety by minimizing human error, optimizing traffic flow, and reducing congestion. Furthermore, AI-driven autonomous vehicles can also improve fuel efficiency and reduce emissions, making transportation more eco-friendly.
However, as with all technological advances, there are inherent associated risks and challenges, such as cybersecurity, which we will explore in the next section.
Benefits of Vehicle Cloud Connectivity
Nowadays, vehicles are interconnected entities constantly communicating with backend servers, typically hosted on cloud platforms. This cloud backend unlocks a wide variety of capabilities for vehicle manufacturers (OEMs). Vehicles can transmit and record sensory data, receive software updates for various Electronic Control Units (ECUs), forward user-initiated requests to and from the vehicle and so much more.
Through the introduction of IoT-centric features, cloud providers equip OEMs with centralized communication and global fleet management tools for hundreds of thousands of vehicles across the globe.
Our PoC attempts to emulate this connectivity using Azure’s IoT Hub and IoT Edge features to deploy updates to the vehicle, including a malicious model. Additionally, our PoC vehicle employs the IoT hub to upload sensory data to the cloud storage, which is used to train new models.
Cybersecurity Risk in the Automotive Industry AI
With the rapid advancement of AI technology in the automotive industry, cybersecurity risks must be addressed. As the presence of autonomous vehicles on our roads becomes more prevalent, the potential for cyber threats increases, posing significant risks to both drivers and pedestrians.
A primary concern regarding AI systems is their vulnerability to malicious attacks. Autonomous vehicles rely heavily on complex AI algorithms and deep learning models to make real-time decisions. However, these systems are susceptible to various types of cyberattacks, such as unauthorized access, data breaches, and even hackers’ remote commandeering of the vehicle.
Another concern is the potential for AI systems to be manipulated or misled by adversarial attacks. These attacks may subtly modify input data, tricking AI models into making incorrect decisions. For autonomous vehicles, even minor changes to sensor data could have severe consequences.
To mitigate these risks, it is crucial for automotive companies to prioritize cybersecurity while developing and deploying AI technology. This means implementing robust encryption protocols, frequent software updates, and conducting regular vulnerability assessments to identify and address potential system weaknesses.
For this purpose, the collaboration of industry leaders, policymakers, and cybersecurity experts is vital for the establishment of industry-wide standards and regulations for autonomous vehicle cybersecurity.
As the automotive industry continues to embrace AI technology, staying vigilant and proactive against cybersecurity risks is essential. By confronting these risks head-on, we can ensure the safe and secure integration of AI in autonomous vehicles and maximize the advantages of this transformative technology.
Cybersecurity Threat – A Real-World Scenario
The following describes the research we conducted to prove the criticality of a vehicle’s onboard decision-making model, the potential harm a compromised model could inflict, and the strategies for preventing such attacks.
An autonomous vehicle runs an object detection model[1]. Through its sensors, it identifies the surrounding objects and makes decisions based on the identification of these objects. Some of the decisions that are influenced by the vehicle’s object identification are illustrated in Figure 1.
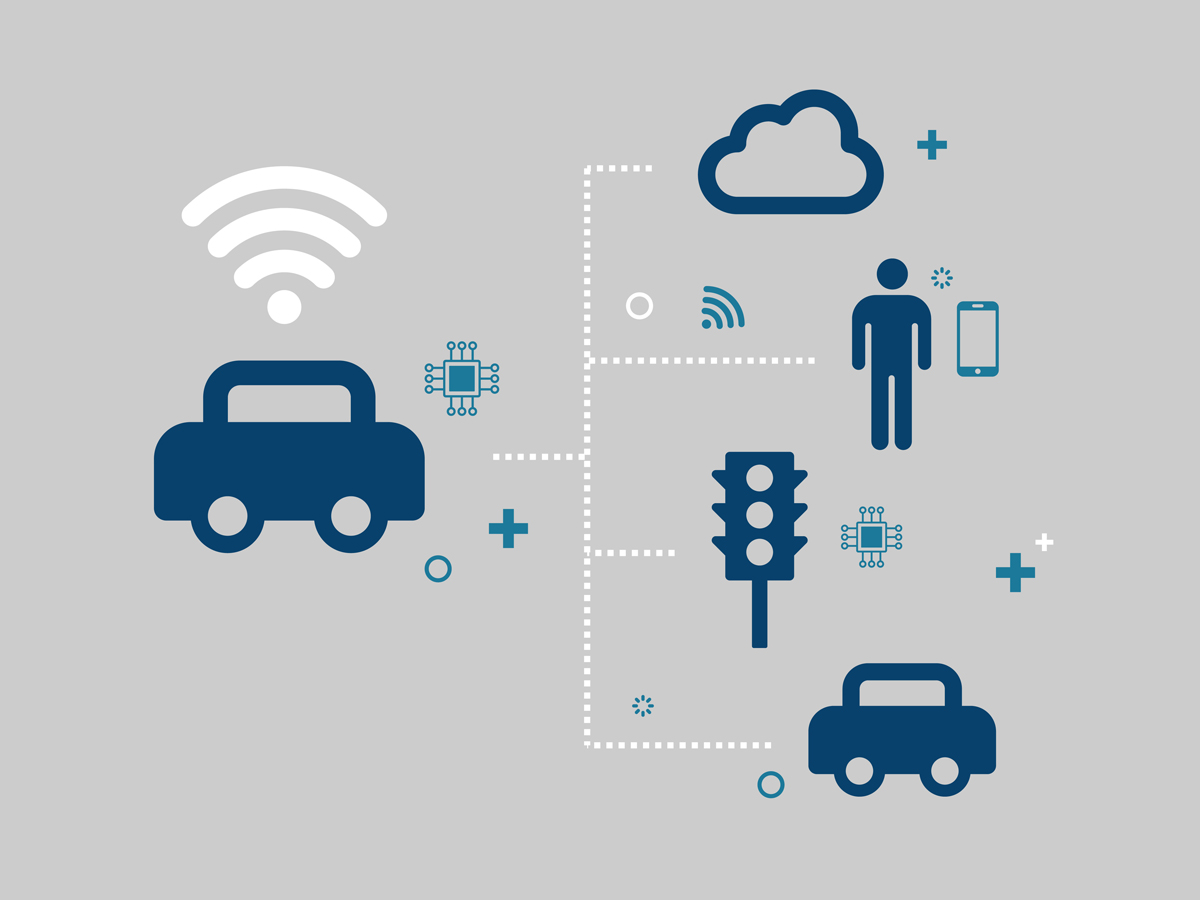
Figure 1
Object identification is based on a model that applies logical rules to the knowledge base to evaluate and analyze new information. This model is trained using relevant data from the vehicle’s environment, which is hosted in the cloud. Deep learning algorithms are employed to identify, classify, and label these objects. The model can then be downloaded to the vehicle. To keep pace with evolving data, rules and regulations, these models undergo regular updates. Using the IoT hub, the model is relayed to the vehicle, which uses it to make decisions and to ensure human safety.
The figure below depicts this process –
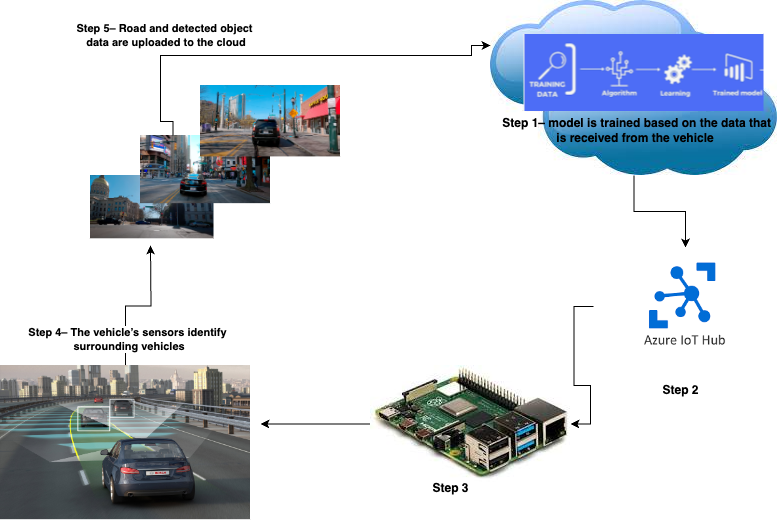
Figure 2
Typical behavior model output appears as follows –
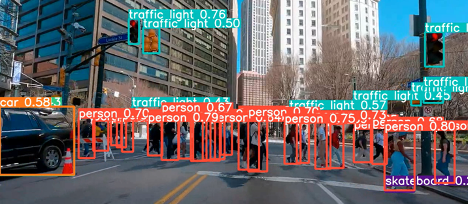
Image 1

Image 2
The images above were captured by the vehicle’s sensors. The surrounding objects were identified by the model and used for subsequent calculations and decisions.
PoC – Exploring Potential Risks and Damage Scenarios of a Compromised Model
The purpose of the PoC is to explore the potential risk and damage scenarios that a compromised model can inflict.
The following describes a scenario where a malicious attacker gains access to the model database hosted in the cloud. The attacker then performs a data-flipping attack, which mislabels pedestrians as vehicles and vehicles as pedestrians. This is achieved by altering the image annotations, such that images labeled as “vehicle” are reclassified as “pedestrian,” and those labeled as “pedestrian” are reclassified as “vehicles.” Once this manipulation is complete, the attacker deploys the altered model to all connected vehicle ECUs, a process simulated by Raspberry Pi in this instance.
In this PoC, we used Azure IoT Hub and IoT Edge to facilitate secure and reliable communication between our backend (our Azure tenant) and Raspberry Pi, which served to simulate a vehicle’s Electronic Control Unit (ECU). The model was initially trained on the Azure backend and then deployed to Raspberry Pi. It was deployed once for the expected behavior, followed by testing. Subsequently, it was deployed again using a malicious model and retested to assess the potential risk.
We used the names of the folders storing the images to label the data set. Images of pedestrians were stored in a pedestrian folder, and likewise for vehicle images. Even a malicious attacker without extensive knowledge of AI could switch folder names and initiate a data-flipping attack. A more sophisticated attacker, however, could cause much more damage and conceal their actions to make them appear naive.
This type of attack would not be possible if the backend (cloud) were properly secured, monitored and logged. If these measures were in place, any changes would trigger alerts in the SIEM/SOC system, and the deployment of the compromised model would have been prevented.
PoC setup:
Step 1– Model is trained based on data that is received from the vehicle.
Step 2– IoT Hub downloads the model to the vehicle.
Step 3– Model is deployed to the vehicle.
Step 4– The vehicle identifies surrounding vehicles.
Step 5– Road detected objects and data are uploaded to the cloud.
The following frames show the road view as received from the vehicle’s sensors and how the compromised model identifies it –

Image 3
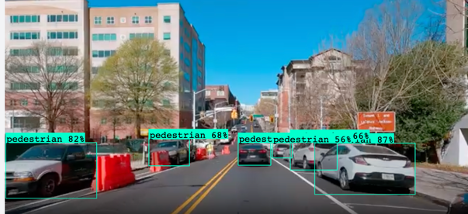
Image 4

Image 5
The vehicle distinctly identified other vehicles as pedestrians and pedestrians as vehicles with an accuracy greater than 70%. Because this is only a PoC, we did not pursue further model training for better results.
Should this scenario represent an actual attack, the potential risk to vehicles and human lives would be extremely high, with the capacity to cause accidents and endanger lives. Furthermore, the effects could extend to an entire fleet of vehicles connected to the same backend.
Summary
This research establishes that connected vehicles have evolved beyond traditional, mechanically controlled systems. This means that the boundaries between the physical vehicle and its virtual counterpart in the cloud backend have become blurred, so that the risks associated with a backend capable of updating a fleet of thousands of vehicles are significantly amplified.
Conclusions
As AI technology becomes an essential component of autonomous vehicles, addressing the cybersecurity risks inherent in this advanced technology is imperative. Collaboration between industry leaders, policymakers, and cybersecurity experts is vital to guarantee the safe and secure integration of AI within the automotive industry. Together, they must establish comprehensive industry-wide standards and regulations recognizing that vehicle security extends beyond the physical vehicle into the interconnected cloud.
By proactively addressing these risks and challenges, we can lay the foundation for a future where AI-powered autonomous vehicles stand out not only for their cutting-edge technological advancements but also for their robust cybersecurity. The future is bright, and by staying vigilant and proactive, we can truly harness the full potential of AI in the automotive industry.
[1] https://universe.roboflow.com/project-tt3kn/object-detection-higqx/model/1?youtube=https%3A%2F%2Fwww.youtube.com%2Fwatch%3Fv%3DB1rC5Ni8Dgk

